An alleged hacker collective that goes by the name Cyber Av3ngers put out a statement on their social media today claiming to have hacked into ten water treatment stations in Israel.
The water stations are located all across the country, according to a map the hackers released, who said that they’d hit targets in Hedera, Palmachim, Sorek, Ashkelon, Haifa, Chorazim, Kfar Haruv, Taberiye, Eilat, and Daniyal.
The Daily Dot couldn’t confirm if any of those locations had actually come under attack. Questions submitted to IDE Technologies about details of the attack weren’t answered. IDE Technologies’ name and logo appear in footage of software menus in a video published by the hacker group purporting to show evidence of the hack. IDE Technologies operates water treatment facilities in some of the locations named by the hackers.
Potable water and the lack there of has been an issue in the conflict, as Israel reportedly shut off access to water to Gaza as it prepped for a ground invasion. The idea of targeting Israeli water treatment facilities could be an act of retaliation.
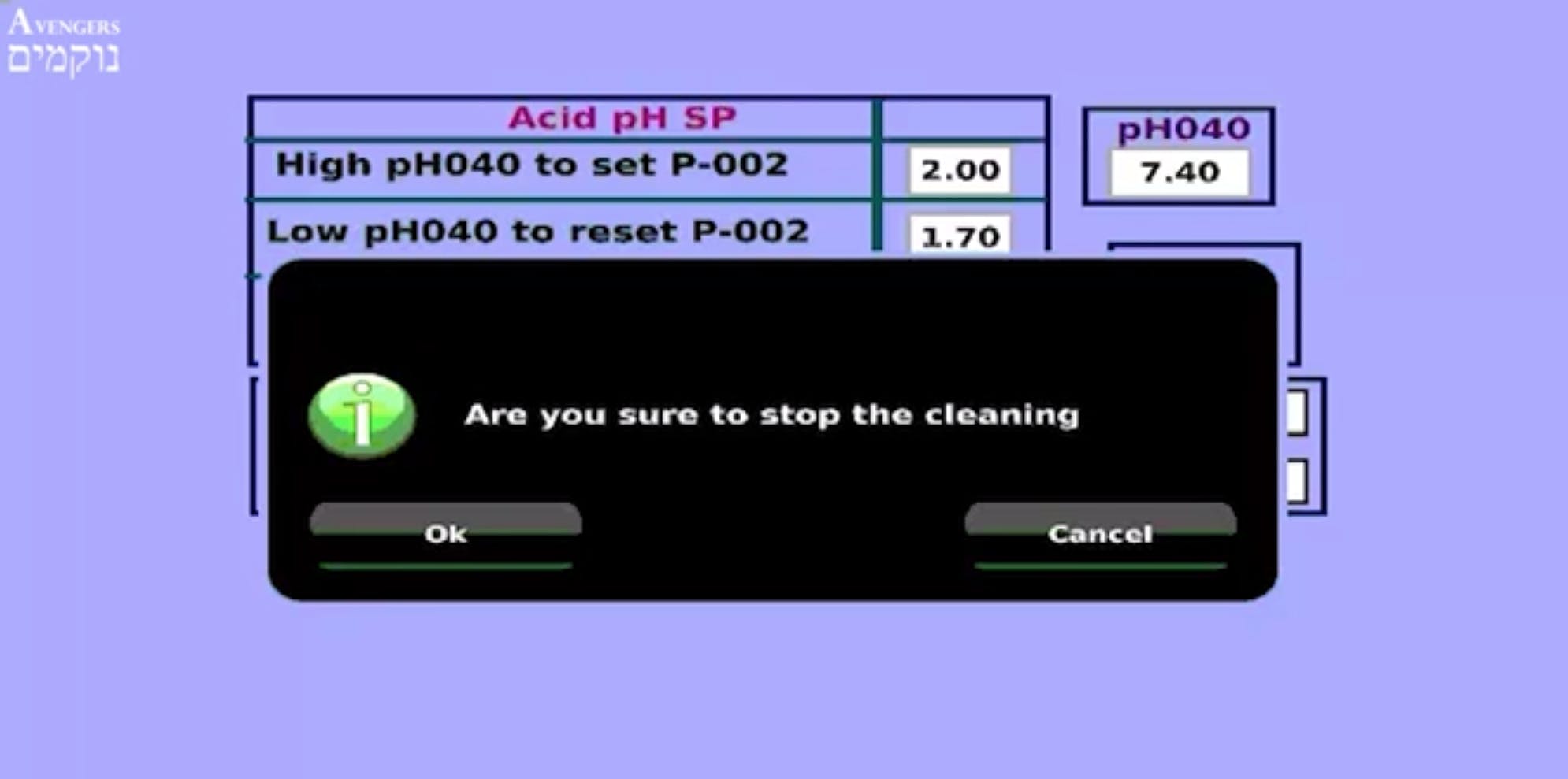
According to that video and statements by the group, the hack knocked out industrial systems that automatically monitor the facilities, sensors, and controls that humans can use to manually operate the system. In one frame of the video, over a menu displaying information about the acidity of the system, a screen asks if the user wants to “stop the cleaning.”
“Definitely,” came the reply from the caption on the video.
The group also posted a detailed video showing how the hack was achieved in a command line terminal, which includes some of the IP addresses associated with the systems that were attacked. The Daily Dot confirmed that those IP addresses were private IP addresses, and the video shows that some of those IP addresses are associated with the company Siemens, which operates some of the software shown in the documentation posted by the group.
Cyber Av3ngers also claimed to be behind cyber attacks on Israeli power stations on Oct. 6, reported Deform.
But an analysis by Securelist by Kaspersky, a cybersecurity company, found that the alleged attack used recycled images and data from a previous attack by a hacktivist group called Moses Staff from 2022. Moses Staff, reported Securelist, is allegedly an Iranian group which tries to damage Israeli companies by “stealing and publishing sensitive data.”
According to Securelist, there’s another active hacker group called “Cyber Avengers” that has been active since 2020, and targets Israeli organizations, “mostly those responsible for operating the critical infrastructure of the country.”
That group though, has no documented links with Cyber Av3ngers.
Sign up to receive the Daily Dot’s Internet Insider newsletter for urgent news from the frontline of online.
Source: https://www.dailydot.com/debug/israel-hacked-cyber-av3engers-water/